Fognigma® and Law Enforcement
Law Enforcement and the Cloud
The International Association of Chiefs of Police (IACP) knows the cloud is becoming more and more important to Law Enforcement (LE). In their Cloud Computing Principles, the IACP explored some very important issues when dealing with the cloud: digital evidence security, portability, data ownership, interoperability, data mining prevention, and cost. Imagine if there was one product that could tackle all these potential pockets of peril and deliver LE the security they need to better serve and protect? There is, and it’s called Fognigma.
Fognigma and Law Enforcement
Fognigma is an enterprise software product which allows an organization to create invisible and encrypted cloud-based networks (called Mission Partner Networks – or MPNs, for short). Inside these MPNs reside a suite of communication and collaboration components (file share, telephony, video conferencing, virtual desktops (VDI), chat, and more) – protected by the same cascading AES-256 encryption that protects every aspect of the MPN. Let’s examine those issues from the Cloud Computing Principles one at a time to showcase how Fognigma can help.

Fognigma Law Enforcement. Secure, encrypted, adaptable comms
Digital Evidence Security
One of Fognigma’s components is encrypted file share. Once users are granted access to the MPN and a file share, they can securely upload files and folders as easily as dragging and dropping on the file share’s user interface. If digital evidence is uploaded directly to the file share, it will not reside on the Law Enforcement Officer’s (LEO’s) computer or mobile device. This capability drastically decreases the chance of lost or compromised evidence. Fognigma can even be implemented in a hybrid formation, if desired, where the file share is physically controlled by LE (i.e., in an LE facility). Fognigma also gives admins granular control of what files users can access and what permissions (read, write, etc.) they have with the files they are allowed to access, which means even more control over digital evidence.
Portability
This one is easy! MPNs can be accessed by any desktop or mobile device using a variety of access controls which work with all major operating systems. Whether it’s a desktop connected with a small piece of hardware or a mobile phone connecting with an app, LEOs can always reach the safety and security of their MPN.
Accessing an MPN on a mobile device
Interoperability
If LE needs to connect with other agencies, organizations, or even informants, Fognigma can help make sure those connections protect every party involved. For example, an informant might be given access to a folder to upload data, but since they were granted access to just that folder, they would be unable to explore (exploit?) anything else on the MPN. Likewise, if multiple agencies need to collaborate in a video conference, they can connect in an MPN without sharing everything on their respective devices and/or networks.
Data Ownership and Data Mining Prevention
Another easy one. Fognigma is owned by you, which means no third parties are needed for oversight, nor have access to your MPN, it’s components, and any data stored within. This is important because many cloud providers are able to view files stored on their servers. With Fognigma, you own it and you run it – no one else is involved. It’s that simple.
Cost
In order to maintain a safe network, organizations have to power a server(s) 24/7, while constantly monitoring for breaches. This takes up a lot of time, money, and resources. Fognigma lets you build MPNs in less than an hour (either manually or scheduled) and destroy them with a few mouse clicks, leaving no forensic footprint. The advantage to this is clear: your MPNs are on only when you need them. Why waste your budget keeping a network running all day/every day if no one needs to use it 24/7?
Other Ways Fognigma Can Help Law Enforcement
The benefits of Fognigma don’t end there. Here are a few more key features which can assist LE:
“Sandboxed” Virtual Desktops (VDIs)
Virtual desktops are an amazing tool for the collection of evidence. They exist as a virtual computer running on, but separate from, the host computer. Using a VDI, LEOs can anonymously browse hostile web environments (i.e., the dark web) while fully obfuscating their true location and identity. Evidence found while browsing on a VDI could easily be copied to a secure file share on an MPN or shared across the network. VDIs are also self-contained for MPN, LAN, and host CPU protection.
Not content to be like other virtual desktops, Fognigma VDIs have several unique features including the ability to transfer data from USB drives directly into VDI environments – completely bypassing the host computer. Also, audio transmitted through a VDI is filtered through a proxy to ensure no IP leaks. Another Fognigma VDI superpower is the ability to have a specially-created folder on a VDI which accesses to a central server and allows the sharing of files between multiple VDI instances. Fognigma VDIs have a preloaded suite of commonly used applications and can be customized with specific apps as needed. They can even act as anonymized entry points onto a Fognigma network, adding even more obfuscation to your location, traffic, intent, etc.
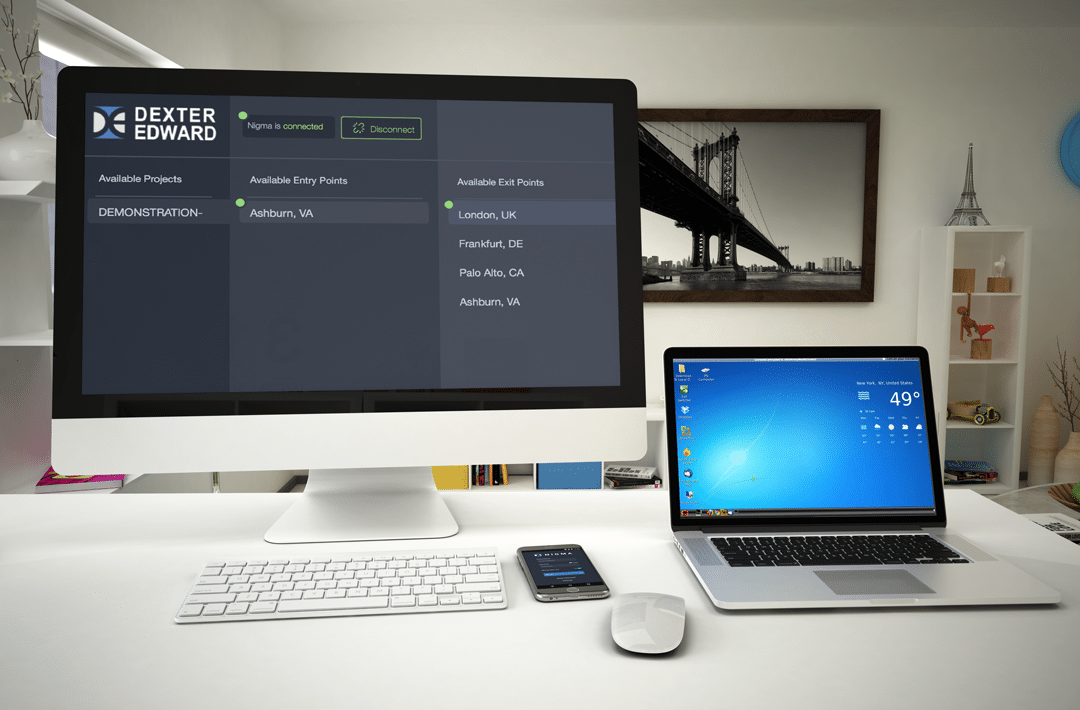
A VDI connected to Fognigma
Traceless Telephony and Misattributable Call Chains
Just like all the other components inside Fognigma, traceless telephony can be set up in a matter of minutes. Create your phone tree inside your MPN and you’ll have end-to-end encrypted VOIP calls over untrusted local infrastructure able to be used to/from any phone anywhere in the world. You could, for example, create a call group where an officer in HQ could dial a three-digit extension and safely reach another member on the team who happens to be five states away (or, in another country, for that matter).
Another key telephony feature of Fognigma is the ability to create misattributable call chains. These call chains are a fantastic way to communicate with an informant without endangering the safety of LE or the informant. They work like this: a chain of four telephone numbers are created – The informant, therefore, never knows the LEO’s true location and phone number – Law Enforcement is protected. And since numbers can be changed at any time, the intermediary number can be switched to something innocuous (such as a movie tip phone number or just an out-of-service number) when not in active use. Then, if the informant’s phone is examined by someone else, the third party won’t be able to tell the informant has been communicating with LE – the informant is also protected.
Fognigma Offers Superior Protection
The Fognigma technology holds three patents for its innovative processes (with more pending) in a time when software patents are very hard to achieve. It is FIPS 140-2 Validated and uses two different software libraries for its dual-layered encryption (OpenSSL and wolfSSL). These are behind-the-scenes advantages of Fognigma – things that might not sound as flashy as the aforementioned misattributable call chains but are just as important for your organization’s protection.
Fognigma provides LE with a whole host of features – from cybersecurity to encrypted communications to secure collaboration. It is much like a police officer’s duty belt: loaded with tools for any situation. And, as the only secure communications platform purposely built to be owned and operated by the customer, Fognigma gives Law Enforcement leading-edge technology so they can better serve and protect into the future.

